Spotify investigates data scraping by Anna’s Archive with 700m users. Leak could benefit AI companies.
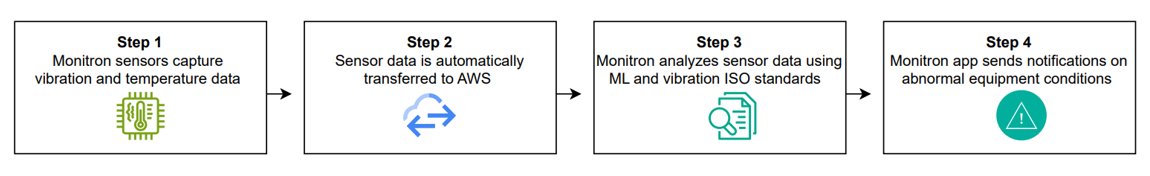
Predictive maintenance uses sensors and analytics to predict machine failures, demonstrated by Amazon using Foundation Models. The solution enhances efficiency and can be customized for various industries, reducing downtime and maximizing performance.
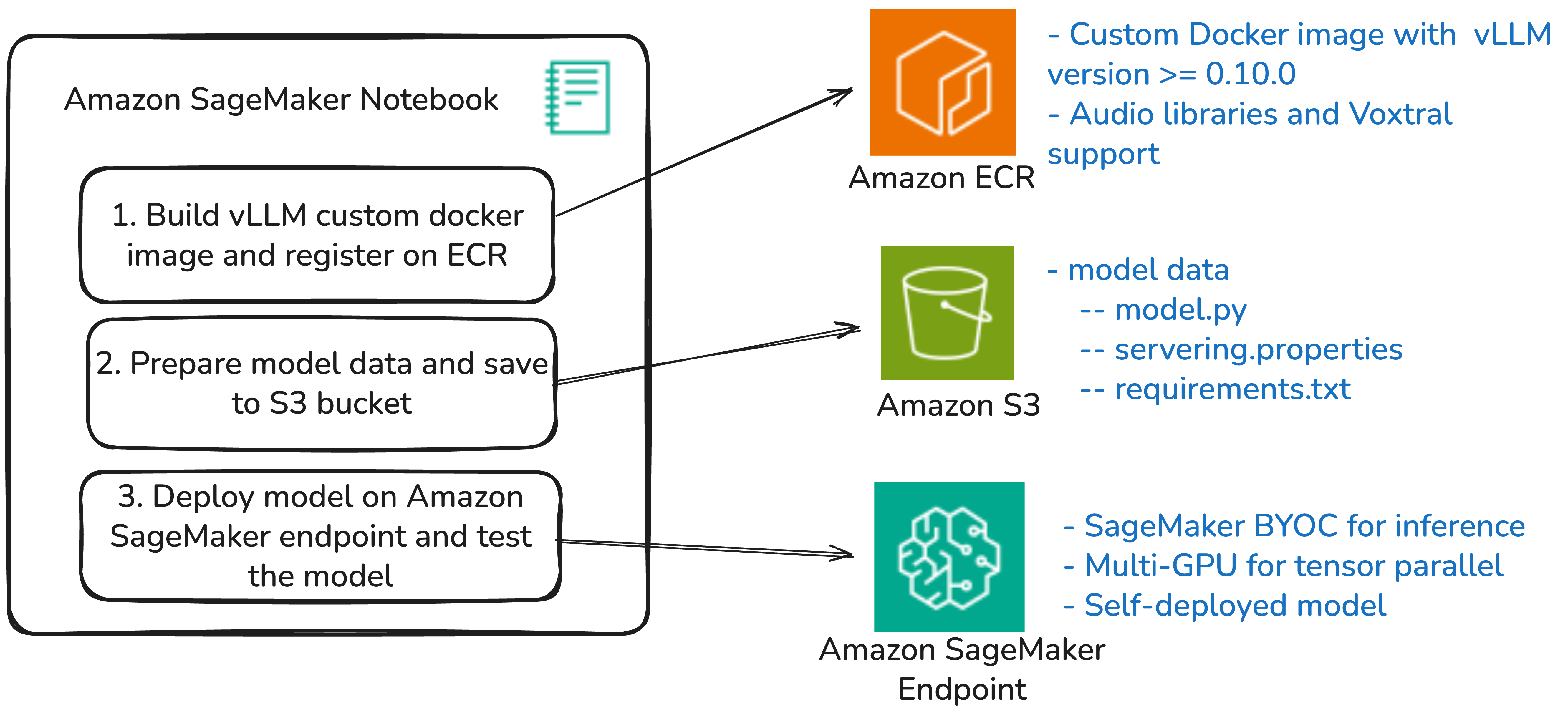
Mistral AI's Voxtral models combine text and audio processing in one framework, with variants optimized for different use cases. These models, hosted on Amazon SageMaker using vLLM and BYOC, offer advanced audio understanding and function calling capabilities for various applications.
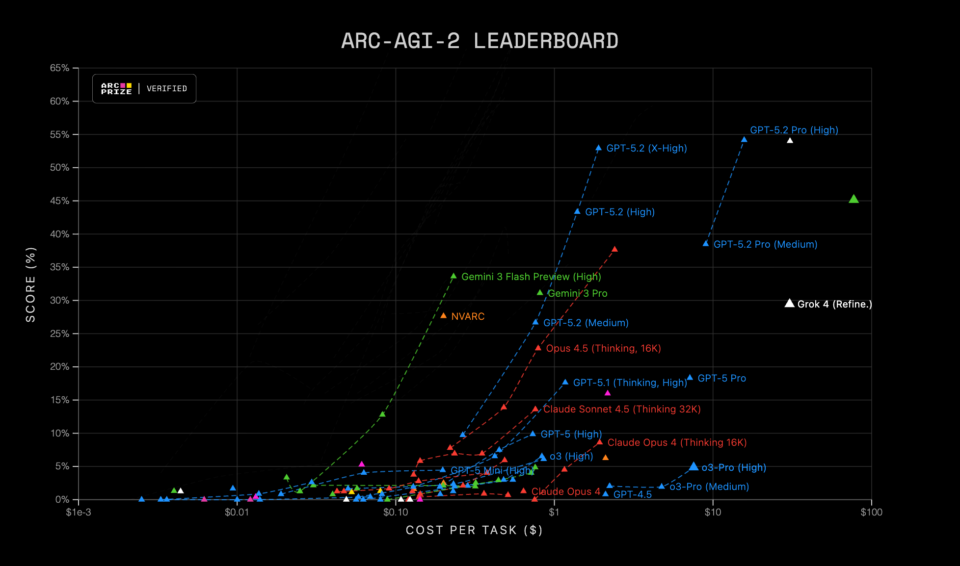
OpenAI launches GPT-5.2, achieving top scores on industry benchmarks with NVIDIA infrastructure. NVIDIA's advanced systems drive down costs and accelerate AI model development, leading to groundbreaking performance gains.
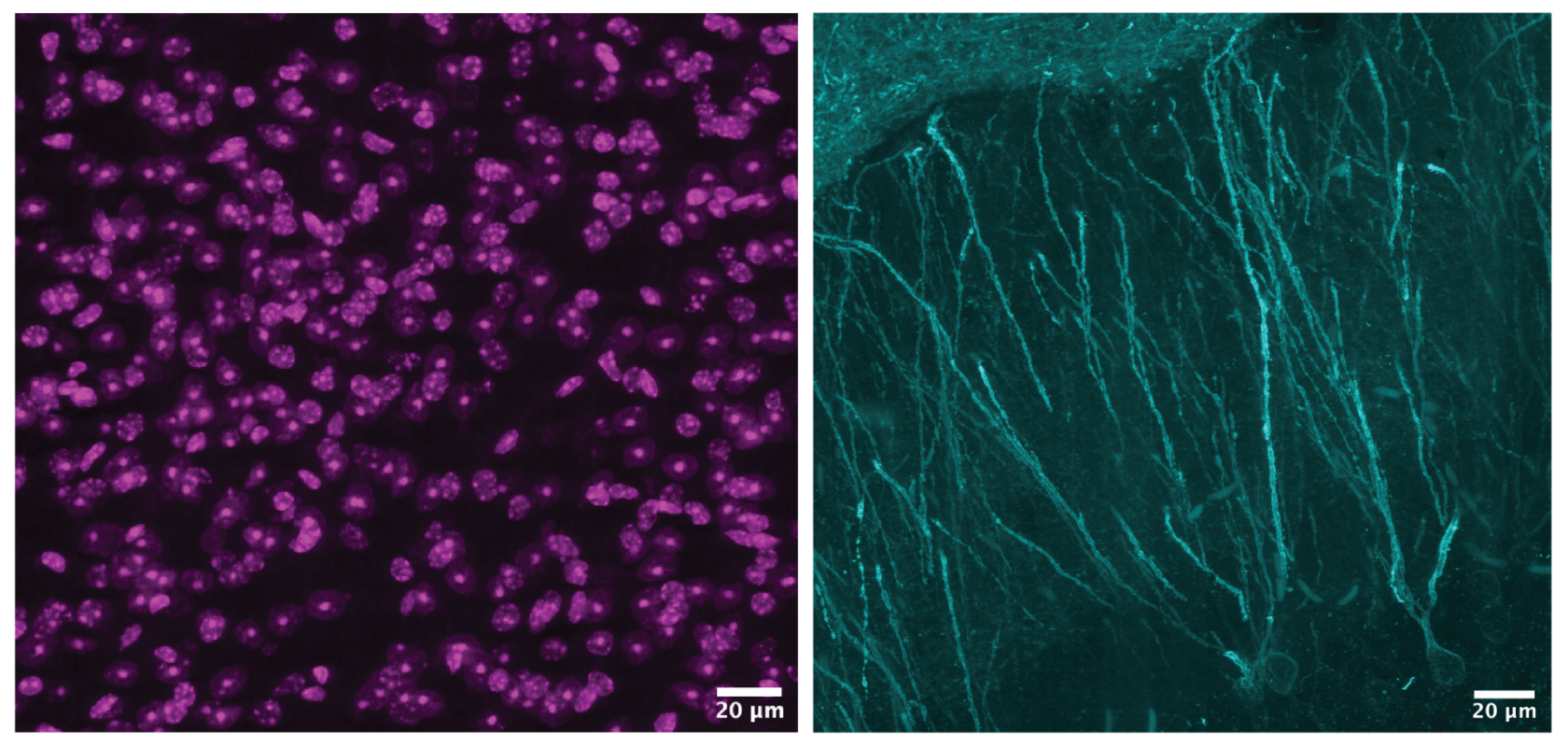
Researchers at MBL study memory formation using NVIDIA RTX GPUs and HP Z Workstations, aiming to unravel molecular-level memory function for potential neurological disease prevention. Understanding memory's role in mental health could lead to breakthroughs in Alzheimer's and dementia research.
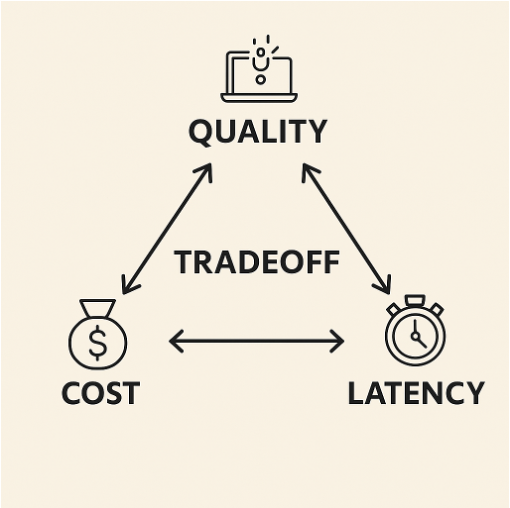
Organizations are seeking efficient AI prompting methods to balance quality, cost, and latency. Chain-of-Draft (CoD) offers a more efficient alternative to traditional prompting, reducing token usage by up to 75% and latency by over 78% while maintaining accuracy levels.
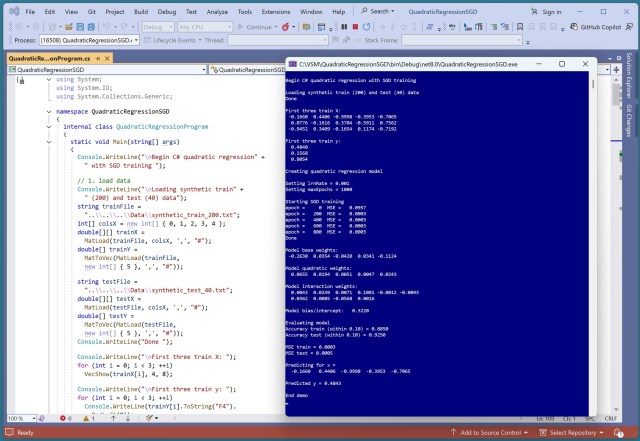
Linear regression is basic but struggles with non-linear data; quadratic regression extends it to handle complexity. A C# demo showcases quadratic regression accuracy, using synthetic data and neural network generation.
Voice generating bots are aiding extremist groups like neo-Nazis and the Islamic State in spreading ideology online. Experts warn that AI tools are evolving digital propaganda strategies, posing a new threat in the fight against terrorism.
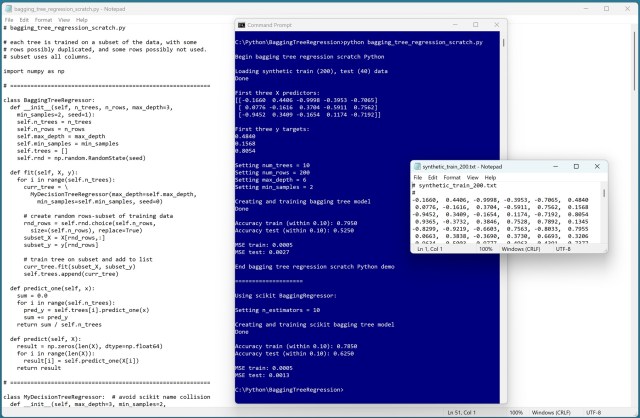
Naive decision tree regression models overfit training data. Bagging and random forest techniques combat overfitting by using subsets for training.
Investment in global data center market hits record $61bn in 2021 amid AI boom, with no signs of slowing down, says S&P Global report. Analysts foresee continued construction frenzy to meet insatiable demand from AI companies, projecting $60.8bn investment by 2024.
Trump Media and Technology Group merges with TAE Technologies in a $6bn deal to combine Truth Social with AI-driven energy solutions. The link-up aims to capitalize on the AI boom and meet the rising energy demand.
Tech companies benefit from AI, but society pays the cost with massive carbon emissions equal to NYC's. Research shows AI's environmental impact surpasses global bottled-water demand.
Productivity Commission drops controversial proposal for tech companies to use copyrighted material for AI training. Government advised to wait 3 years before reviewing Australian copyright settings and impact of new technology.
AI accelerates ML development by determining techniques, generating code, and tuning hyperparameters, cutting model creation time significantly. AI may increase data science efficiency, but impact entry-level positions, while generating creative outputs like a steampunk car.
MIT CSAIL researchers found that short-term guidance can significantly enhance the performance of previously deemed "ineffective" neural networks by aligning internal representations. Unlike knowledge distillation, guidance transfers structural knowledge directly, leveraging untrained networks' architectural biases for effective learning.